Sonicwall
SonicWall Network Security Virtual (NSV) 800 Virtual Appliance
Many in stock
Datasheet
The design, implementation and deployment of modern network architectures, such as virtualization and cloud, continue to be a game-changing strategy for many organizations. Virtualizing the data center, migrating to the cloud, or a combination of both, demonstrates significant operational and economic advantages. However, vulnerabilities within virtual environments are well-documented. New vulnerabilities are discovered regularly that yield serious security implications and challenges. To ensure applications and services are delivered safely, efficiently and in a scalable manner, while still combating threats harmful to all parts of the virtual framework including virtual machines (VMs), application workloads and data must be among the top priorities.
The SonicWall Network Security virtual (NSv) firewall series helps security teams reduce these types of security risks and vulnerabilities, which can cause serious disruption to your business-critical services and operations. NSv nextgeneration virtual firewalls integrate two advanced security technologies to deliver cutting-edge threat prevention that keeps your network one step ahead. SonicWall’s patent-pending Real-Time Deep Memory Inspection (RTDMI™) technology enhances our award-winning multi-engine Capture Advanced Threat Protection (ATP) sandboxing service. The RTDMI engine proactively detects and blocks mass market, zero-day threats and unknown malware by inspecting directly in memory. Because of the real-time architecture, SonicWall RTDMI technology is precise, minimizes false positives, and identifies and mitigates sophisticated attacks where the malware’s weaponry is exposed for less than 100 nanoseconds. In combination, SonicWall’s patented* single-pass Reassembly-Free Deep Packet Inspection (RFDPI®) engine examines every byte of every packet, inspecting both inbound and outbound traffic on the firewall.
*U.S. Patents 7,310,815; 7,600,257; 7,738,380; 7,835,361; 7,991,723
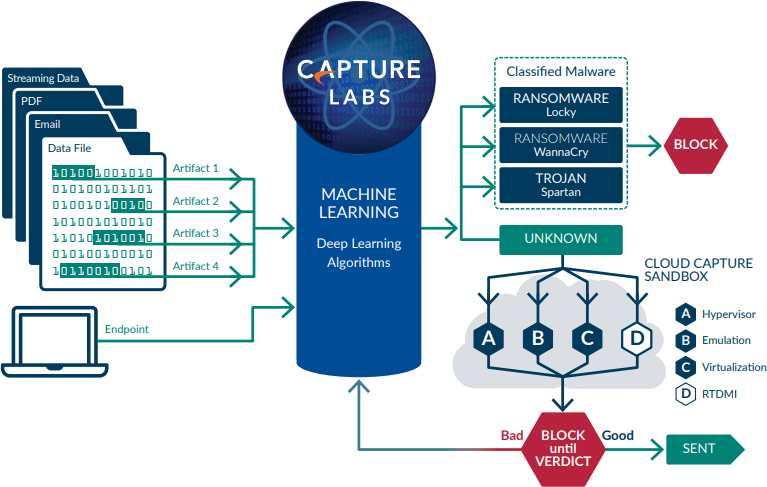
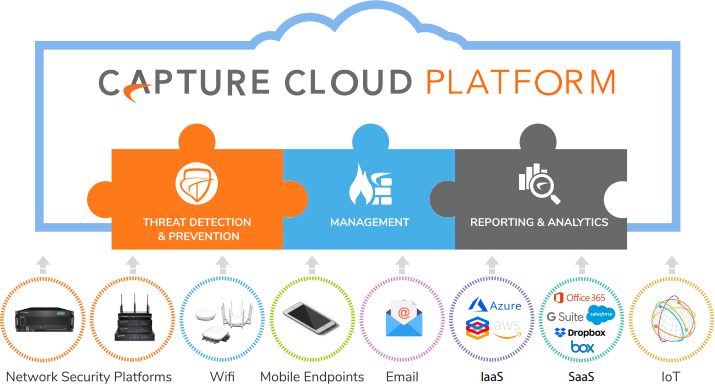
The NSv series delivers the automated real-time breach detection and prevention organizations need by utilizing innovative deep learning technologies in the SonicWall Capture Cloud Platform. This platform delivers cloud-based threat prevention and network management plus reporting and analytics for organizations of any size. This platform consolidates threat intelligence gathered from multiple sources including our Capture ATP, as well as more than 1 million SonicWall sensors located around the globe. By leveraging the SonicWall Capture Cloud Platform in addition to capabilities including intrusion prevention, antimalware and web/URL filtering, the NSv series blocks even the stealthiest threats at the gateway.
NSv is easily deployed and provisioned in a virtual environment, typically between virtual networks (VNs) or virtual private clouds (VPCs). This allows it to capture communications and data exchanges between virtual machines for automated breach prevention, while establishing stringent access control measures for data confidentiality and VM safety and integrity. Security threats (such as crossvirtual-machine or side-channel attacks, common network-based intrusions, and application and protocol vulnerabilities) are neutralized successfully through SonicWall’s comprehensive suite of security inspection services1. All VM traffic is subjected to multiple threat analysis engines, including intrusion prevention, gateway anti-virus and antispyware, cloud anti-virus, botnet filtering, application control and Capture ATP multi-engine sandboxing with RTDMI technology.
Segmentation Security
For optimal effectiveness against Advanced Persistent Threats (APTs), network security segmentation must apply an integrated set of dynamic, enforceable barriers to advanced threats. With segment-based security capabilities, NSv can group similar interfaces and apply the same policies to them, instead of having to write the same policy for each interface. By applying security policies to the inside of the VN, segmentation can be configured to organize network resources into different segments, and allow or restrict traffic between those segments. This way, access to critical internal resources can be strictly controlled.
NSv automatically enforces segmentation restrictions based upon dynamic criteria, such as user identity credentials, geoIP location and the security stature of mobile endpoints. For extended security, NSv is also capable of integrating multi-gigabit network switching into its security segment policy and enforcement. It directs segment policy to traffic at switching points throughout the network, and globally manages segment security enforcement from a single pane of glass.
Since segments are only as effective as the security that can be enforced between them, NSv applies intrusion prevention system (IPS) to scan incoming and outgoing traffic on the VLAN segment to enhance security for internal network traffic. For each segment, it enforces a full range of security services on multiple interfaces based on enforceable policy.
Flexible Deployment Use Cases
With infrastructure support for high availability implementation, NSv fulfills scalability and availability requirements of Software Defined Data Centers. It ensures system resiliency, service reliability, and regulatory conformance. Optimized for broad range of public, private and hybrid deployment use cases, NSv can adapt to service-level changes and ensure VMs and their application workloads and data assets are available, as well as secure. It can do it all at multiGbps speed with low latency.
Organizations gain all the security advantages of a physical firewall, with the operational and economic benefits of virtualization. This includes system scalability, operation agility, provisioning speed, simple management and cost reduction.
The NSv series is available in multiple virtual flavors carefully packaged for a broad range of virtualized and cloud deployment use cases. Delivering multigigabit threat prevention and encrypted traffic inspection performance, the NSv series adapts to capacity-level increases and ensures VN and VPC safety. The series also ensures application workloads and data assets are available as well as secure.
Govern Centrally
NSv deployments can be centrally managed either on premises with SonicWall Global Management System (GMS²), or with Capture Security Center², SonicWall’s open, scalable cloud security management, monitoring, reporting and analytics platform delivered as a costeffective as-a-service offering.
Capture Security Center gives the ultimate in visibility, agility and capacity to govern the entire SonicWall virtual and physical firewall ecosystem with greater clarity, precision, and speed – all from a single pane of glass.
Flexible Licensing
NSv supports Bring Your Own License (BYOL) and Pay As You Go (PAYG) licensing. The BYOL license for NSv can be purchased directly from SonicWall, a partner or reseller. Whereas, PAYG license is purchased directly from the AWS Marketplace. This type of license is a usage-based license wherein payment is made as per usage on an hourly or annual basis.
GOVERN CENTRALLY
- Establish an easy path to comprehensive security management, analytic reporting and compliance to unify your network security defense program
- Automate and correlate workflows to form a fully coordinated security governance, compliance and risk management strategy
COMPLIANCE
- Make regulatory bodies and auditors happy with automatic PCI, HIPAA and SOX security reports
- Customize any combination of security auditable data to help you move towards specific compliance regulations
RISK MANAGEMENT
- Move fast and drive collaboration, communication and knowledge across the shared security framework
- Make informed security policy decisions based on time-critical and consolidated threat information for higher level of security efficiency
GMS provides a holistic approach to security governance, compliance and risk management
Pricing Notes:
- Pricing and product availability subject to change without notice.
Returns Policy
Unless otherwise stated below, you have 30 days from the date your product left the warehouse (regardless of when you actually took delivery of the product) to get a valid RMA from our website and get your product to a shipper to return back to us. It does not have to be back in our warehouse within 30 days, but it does have to be in the possession of the shipper (along with the valid RMA). RMAs must be valid, unexpired, and issued for the product being returned. Only one RMA is issued per return. When it expires, you may no longer return your product. If you are ineligible for an RMA, contact the manufacturer directly or check any applicable warranty you might have. See the Manufacturer Contact List at the bottom of this page. Except as provided for verified defective products (See Special Returns Policy for Defective Products below), you will be responsible for all shipping charges for returns sent to our Returns Warehouse. All products are subject to a 15% restocking fee (except where prohibited by law) if returned opened or in a non-factory sealed box, provided that there is no restocking fee for defective products (see Special Returns Policy for Defective Products below). Upon our acceptance of the merchandise in like new condition in strict conformance with the basic criteria and basic returns policy, the purchase price will be credited to the credit card used for the original purchase. Please allow up to fourteen days from shipment for your return to arrive at our Returns Warehouse, delivery times vary based on shipper selected. Your return will be processed within 5-7 business days (excluding Saturdays, Sundays, and holidays) after receipt of the item. Many of the items we sell have Special Return Policies. See the appropriate policy below to see if items you purchase are affected. The risk of loss for the product being returned shall be with you at all times during the shipment of such product to the returns center and with respect to any shipments from the returns center back to you, the original distributor or manufacturer, or any buyer through the liquidation process. Title to the product being returned will remain with you at all times and transfer from you to the original distributor, or a third party in the case of a liquidation of the return, only upon receipt of the products by such distributors or buyers.
Defective Products
Defective products can only be returned in exchange for the exact same product, or at the sole discretion of Protective Data Solutions, the purchase price will be credited to the credit card used for the original purchase. Defective products may only be returned within 30 days of the date your product left the warehouse (regardless of when you actually took delivery of the product). Once your return is processed, and is verified to meet the basic criteria above and to be defective, your replacement order will be sent to fulfillment. How quickly your replacement product ships after that depends on product availability. For products that we verify to be defective, we will reimburse you for your original shipping expenses, provided that your defective return must be shipped via ground shipment only. If you return your product via a faster, more expensive shipper, you incur the expenses yourself and any request for reimbursement will be denied. Protective Data Solutions in its sole and absolute discretion shall be the sole determiner of whether a product is in fact defective.
Shipping
We can ship to virtually any address in the world. Note that there are restrictions on some products, and some products cannot be shipped to international destinations.
When you place an order, we will estimate shipping and delivery dates for you based on the availability of your items and the shipping options you choose. IF THE ITEM IS A LICENSE OR RENEWAL, e-Deliveries will be processed the same business day. Depending on the shipping provider you choose, shipping date estimates may appear on the shipping quotes page.
Please also note that the shipping rates for many items we sell are weight-based. The weight of any such item can be found on its detail page. To reflect the policies of the shipping companies we use, all weights will be rounded up to the next full pound.
Discounts
Bulk discounting is available, so give us a call or email us at sales@protectivedatasolutions.com and we can build you a custom quote and see if we can save you even more off the advertised price.Payment Options
You may also pay via Cashiers Check, Bank Wire, and more. Contact us for other payment options.


























